grouper-users - [grouper-users] grouper 2.2 security xss vulnerability in tooltips in new UI
Subject: Grouper Users - Open Discussion List
List archive
- From: Chris Hyzer <>
- To: "" <>
- Subject: [grouper-users] grouper 2.2 security xss vulnerability in tooltips in new UI
- Date: Wed, 18 Nov 2015 05:42:12 +0000
- Accept-language: en-US
- Importance: high
|
Grouper-users, HTML in the display path or description in grouper objects can be exploited with XSS in tooltips in the Grouper “new UI” (v2.2+). It is recommended that you address this issue as soon as you can. I don’t want to get into how to exactly
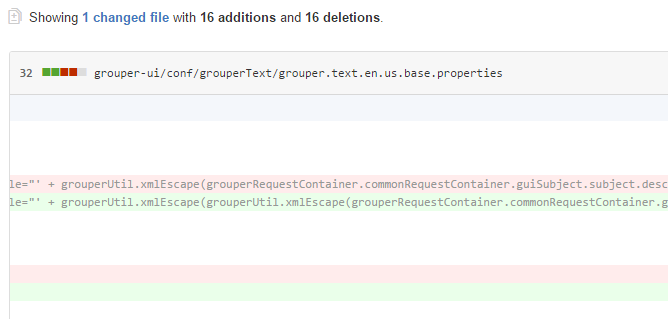
reproduce this, if you want the steps contact me directly (it’s not that complicated). There is a patch for 2.2.2: grouper_v2_2_2_ui_patch_4. Note, this patch does not require a restart of the Grouper UI to take effect (though you might need to wait a minute or two). If you are on 2.2.0 or 2.2.1, you can either upgrade to 2.2.2 including patches, or you can just edit the file per the commit below: grouper.text.en.us.base.properties https://bugs.internet2.edu/jira/browse/GRP-1222 https://github.com/Internet2/grouper/commit/8b14c0a6e8ceb9e138f3b9ae2d7f865375daca47 Data in tooltips in the new UI are escaped for HTML, but they need to be escaped twice. The patch will change the templates that display grouper objects to escape twice like the commit in thie jira (e.g. below).
If you have any questions about this please contact me directly, or via list if it is not a sensitive message. Thanks to Josh Kwan from Berkeley for reporting this a few hours ago. Thanks to Vivek Sachdeva for reviewing the fix on short notice. The Grouper demo server is patched and tested. Thanks, Chris Here is an example of the escaping. Note the xmlEscape function is called twice for tooltips, if you call it once, it will be valid HTML and the rendered HTML will display on the page which obviously is bad, if you call it twice, then
the HTML source will display on the page which is what we want.
|
- [grouper-users] grouper 2.2 security xss vulnerability in tooltips in new UI, Chris Hyzer, 11/18/2015
Archive powered by MHonArc 2.6.16.